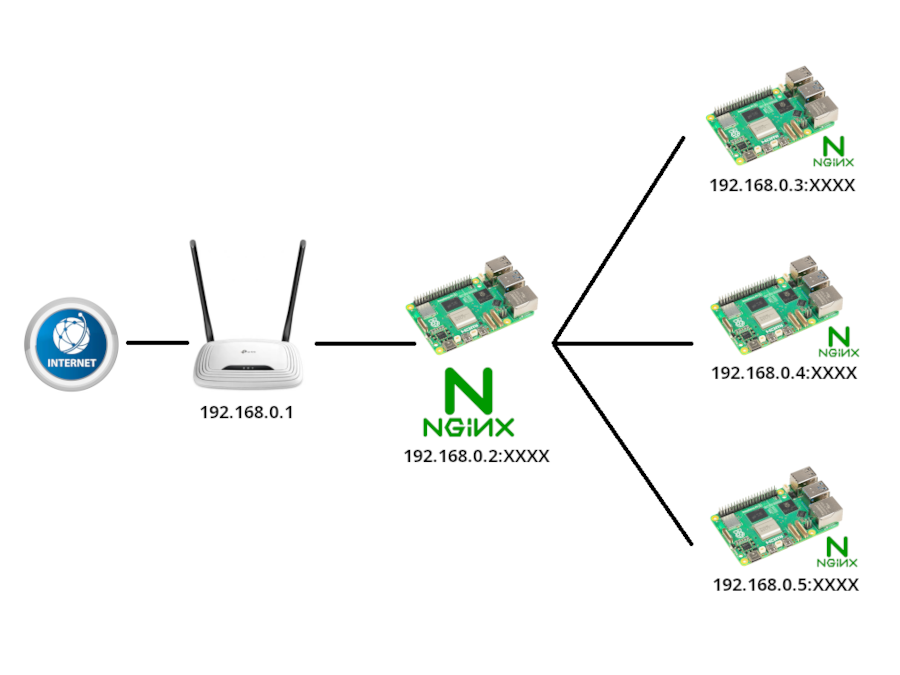
Ací et deixe com tinc configurada la Raspberry Pi principal i la Raspberry Pi amb una IP distinta i que ofereix projectes de PHP.
Raspberry Pi principal amb configuracions de proxy invers en altres Raspberry Pi interiors
En aquesta Raspberry Pi generarem el certificat SSL amb Let's Encrypt per a que accepte HTTPS en el port 443 sense problemes. I així aconseguisc muntar webs en màquines Raspberry Pi interiors que no es veuen des de fora del router per que, mitjançant l'Nginx de la Raspberry Pi principal, faig una redirecció de proxy invers en el port 80 o 443 per a diversos projectes web sense fer la càrrega en la Raspberry Pi principal:
I també, la configuració que tinc a Nginx de la Raspberry Pi principal que em fa de proxy invers. Editarem el fitxer /usr/local/etc/nginx/sites-enabled/astrofotografia.joancatala.net i afegirem el següent:
server {
server_name ACÍ_EL_TEU_DOMINI;
location / {
proxy_pass https://ACÍ_LA_IP_DE_LA_MÀQUINA_INTERNA/;
proxy_ssl_verify off;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /usr/local/etc/letsencrypt/live/ACÍ_EL_TEU_DOMINI/fullchain.pem; # managed by Certbot
ssl_certificate_key /usr/local/etc/letsencrypt/live/ACÍ_EL_TEU_DOMINI/privkey.pem; # managed by Certbot
include /usr/local/etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /usr/local/etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = ACÍ_EL_TEU_DOMINI) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
server_name ACÍ_EL_TEU_DOMINI;
return 404; # managed by Certbot
}
La Raspberry Pi 2 amb projectes PHP
En aquesta Raspberry ficarem la configuració Nginx que tenim en /usr/local/etc/nginx/sites-enabled/astrofotografia.joancatala.net següent:
server {
server_name ACÍ_EL_TEU_DOMINI;
root /usr/local/www/ACÍ_LA_RUTA_ON_TENS_LA_WEB; ## -- Your only path reference.
location = /favicon.ico {
log_not_found off;
access_log off;
}
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
# Very rarely should these ever be accessed outside of your lan
location ~* \.(txt|log)$ {
allow 192.168.0.0/16;
deny all;
}
location ~ \..*/.*\.php$ {
return 403;
}
location ~ ^/sites/.*/private/ {
return 403;
}
# Block access to scripts in site files directory
location ~ ^/sites/[^/]+/files/.*\.php$ {
deny all;
}
# Allow "Well-Known URIs" as per RFC 5785
location ~* ^/.well-known/ {
allow all;
}
# Block access to "hidden" files and directories whose names begin with a
# period. This includes directories used by version control systems such
# as Subversion or Git to store control files.
location ~ (^|/)\. {
return 403;
}
# Aci abans estava la configuracio del "location /" que
# feia de proxy invers a Mercuri (192.168.1.X) pero ara
# que ja estem a Urà (192.168.1.X) ja puc configurar el Nginx
# com el tenia configurat al inici, que es el seguent:
location / {
# try_files $uri @rewrite; # For Drupal = 6
try_files $uri /index.php?$query_string; # For Drupal >= 7
}
location @rewrite {
#rewrite ^/(.*)$ /index.php?q=$1; # For Drupal = 6
rewrite ^ /index.php; # For Drupal >= 7
}
# Don't allow direct access to PHP files in the vendor directory.
location ~ /vendor/.*\.php$ {
deny all;
return 404;
}
# Protect files and directories from prying eyes.
location ~* \.(engine|inc|install|make|module|profile|po|sh|.*sql|theme|twig|tpl(\.php)?|xtmpl|yml)(~|\.sw[op]|\.bak|\.orig|\.save)?$|^(\.(?!well-known).*|Entries.*|Repository|Root|Tag|Template|composer\.(json|lock)|web\.config)$|^#.*#$|\.php(~|\.sw[op]|\.bak|\.orig|\.save)$ {
deny all;
return 404;
}
# In Drupal 8, we must also match new paths where the '.php' appears in
# the middle, such as update.php/selection. The rule we use is strict,
# and only allows this pattern with the update.php front controller.
# This allows legacy path aliases in the form of
# blog/index.php/legacy-path to continue to route to Drupal nodes. If
# you do not have any paths like that, then you might prefer to use a
# laxer rule, such as:
# location ~ \.php(/|$) {
# The laxer rule will continue to work if Drupal uses this new URL
# pattern with front controllers other than update.php in a future
# release.
location ~ '\.php$|^/update.php' {
fastcgi_split_path_info ^(.+?\.php)(|/.*)$;
# Ensure the php file exists. Mitigates CVE-2019-11043
try_files $fastcgi_script_name =404;
# Security note: If you're running a version of PHP older than the
# latest 5.3, you should have "cgi.fix_pathinfo = 0;" in php.ini.
# See http://serverfault.com/q/627903/94922 for details.
include fastcgi_params;
# Block httpoxy attacks. See https://httpoxy.org/.
fastcgi_param HTTP_PROXY "";
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param QUERY_STRING $query_string;
fastcgi_intercept_errors on;
# PHP 5 socket location.
#fastcgi_pass unix:/var/run/php5-fpm.sock;
# PHP 8.2 socket location.
fastcgi_pass unix:/var/run/php82-fpm.sock;
}
location ~* \.(js|css|png|jpg|jpeg|gif|ico|svg)$ {
try_files $uri @rewrite;
expires max;
log_not_found off;
}
# Fighting with Styles? This little gem is amazing.
# location ~ ^/sites/.*/files/imagecache/ { # For Drupal = 6
location ~ ^/sites/.*/files/styles/ { # For Drupal >= 7
try_files $uri @rewrite;
}
# Handle private files through Drupal. Private file's path can come
# with a language prefix.
location ~ ^(/[a-z\-]+)?/system/files/ { # For Drupal >= 7
try_files $uri /index.php?$query_string;
}
# Enforce clean URLs
# Removes index.php from urls like www.example.com/index.php/my-page --> www.example.com/my-page
# Could be done with 301 for permanent or other redirect codes.
if ($request_uri ~* "^(.*/)index\.php/(.*)") {
return 307 $1$2;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /usr/local/etc/letsencrypt/live/ACÍ_EL_TEU_DOMINI/fullchain.pem; # managed by Certbot
ssl_certificate_key /usr/local/etc/letsencrypt/live/ACÍ_EL_TEU_DOMINI/privkey.pem; # managed by Certbot
include /usr/local/etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /usr/local/etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = ACÍ_EL_TEU_DOMINI) {
return 301 https://$host$request_uri;
} # joan
server_name ACÍ_EL_TEU_DOMINI;
listen 80;
return 404; # joan
}
MÉS ARTICLES RELACIONATS
- Configurar proxy invers a Nginx per tenir diferents Raspberry Pi i diferents IP i projectes
- Configurant certificat SSL per a la navegació HTTPS a les màquines darrerre del proxy invers
- Configurant Drupal 11 en una Raspberry Pi 4 darrere d’un proxy invers Nginx





